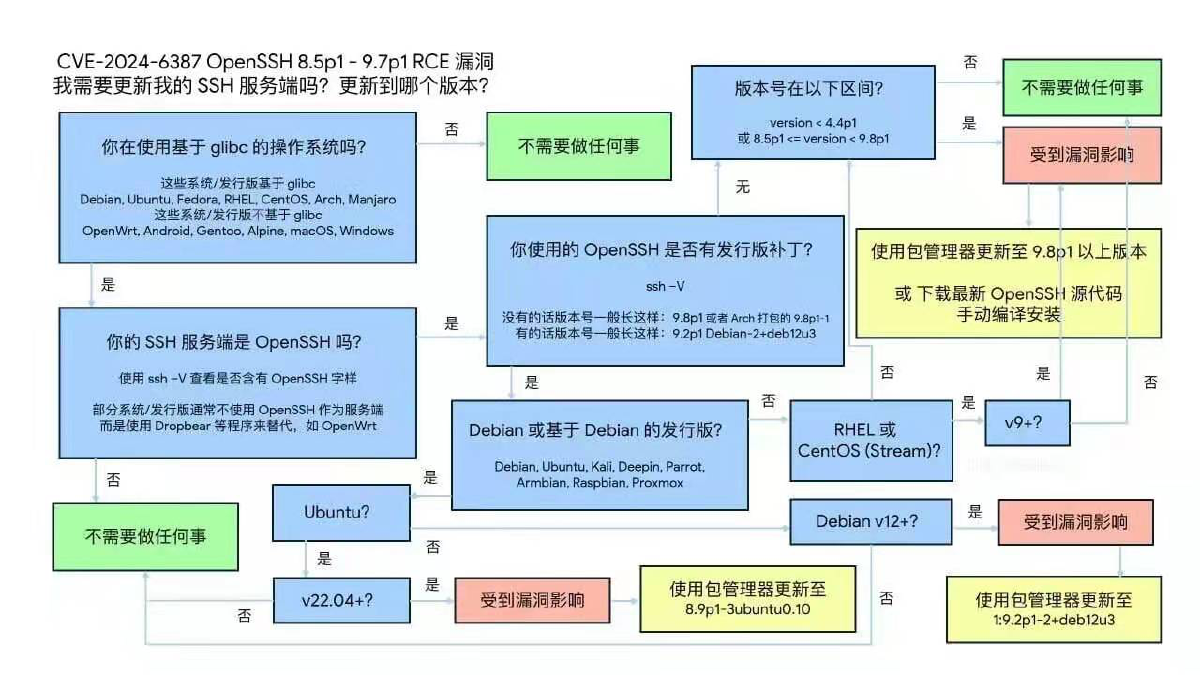
Vulnerability description, CVE-2024-6387: https://nvd.nist.gov/vuln/detail/CVE-2024-6387
This basically affects newer versions of operating systems. Older systems like CentOS 7.9, RockyLinux 8.9, Ubuntu 20.04, Debian 11 escaped this due to older OpenSSH versions.
Among the operating system distributions supported by Pigsty, RockyLinux 9.3, Ubuntu 22.04, and Debian 12 are affected:
ssh -V
OpenSSH_8.7p1, OpenSSL 3.0.7 1 Nov 2022 # rockylinux 9.3
OpenSSH_8.9p1 Ubuntu-3ubuntu0.6, OpenSSL 3.0.2 15 Mar 2022 # ubuntu 22.04
OpenSSH_9.2p1 Debian-2+deb12u2, OpenSSL 3.0.11 19 Sep 2023 # debian 12Diagnosis Method#
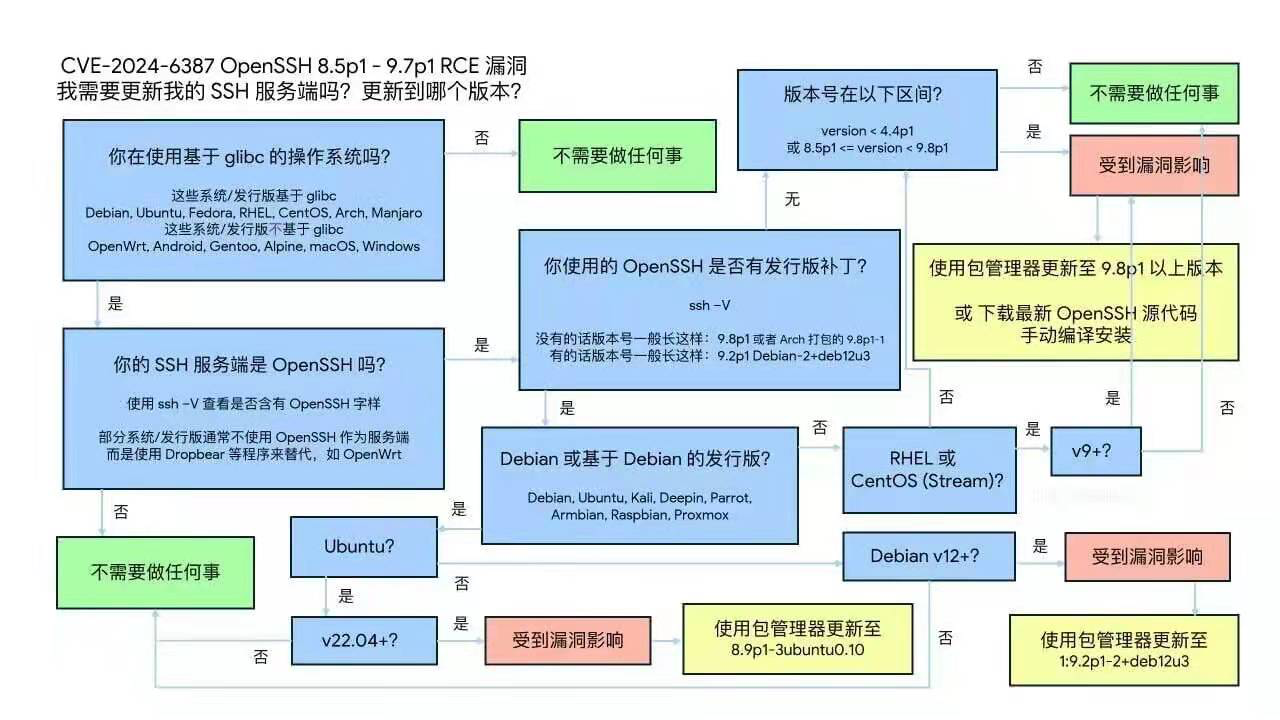
Vulnerability announcements:
RockyLinux 9+: https://rockylinux.org/news/2024-07-01-openssh-sigalrm-regression
Debian 12+: https://security-tracker.debian.org/tracker/CVE-2024-6387
Ubuntu 22.04+: https://ubuntu.com/security/CVE-2024-6387
Solution#
Use the system’s default package manager to upgrade openssh-server.
Post-upgrade version reference:
# rockylinux 9.3 : 8.7p1-34.el9 -------> 8.7p1-38.el9_4.1
# ubuntu 22.04 : -------> 8.9p1-3ubuntu0.6
# debian 12 : -------> 1:9.2p1-2+deb12u2 systemctl restart sshdrocky9.3#
$ rpm -q openssh-server
openssh-server-8.7p1-34.el9.x86_64 # vulnerable
$ yum install openssh-server
openssh-server-8.7p1-38.el9_4.1.x86_64 # fixeddebian12#
$ dpkg -s openssh-server
$ apt install openssh-server
Version: 1:9.2p1-2+deb12u2 # fixedubuntu22.04#
$ dpkg -s openssh-server
$ apt install openssh-server
Version: 1:8.9p1-3ubuntu0.6Future Improvements#
In Pigsty’s next version v2.8, the latest version of openssh-server will be downloaded and installed by default, thus fixing this vulnerability.